Cybersecurity attacks are on the rise. The majority of these attacks involve malware, but phishing attacks(new window) are also a major concern. The Anti-Phishing Working Group (APWG) saw over 1 million phishing attacks(new window) in the first quarter of 2022 alone, an unprecedented total.
Small to medium-sized businesses (SMB’s) may think they are too small to target, but a recent report from Acronis(new window) shows that they’re increasingly vulnerable due to increases in cyberattack automation. The primary attack vector is phishing, with 94% of malware coming via email.
The security outfit Kaspersky’s estimates(new window) the cost of cyberattacks to SMBs at around $86,500 and enterprises at “a staggering” $861,000. These figures take all factors into account, including lost business, additional money spent on public relations, hiring professional IT staff to fix the problem, and so on.
Small businesses are particularly vulnerable to cybersecurity attacks because they rarely have the resources to mitigate them or the know-how to prevent them. According to the UK government report, the primary vector for 83% of cyberattacks is via email (phishing). This is particularly concerning because 92% of data breaches result from phishing attacks(new window).
And the number of these data breaches has increased dramatically, with reports from the first quarter of 2022 showing a “cyberdemic(new window)” affecting all levels of business, including big-name companies such as LastPass, Plex, Cisco, Uber, Plex, Verizon, and many more(new window).
This article discusses how email-based cyberattacks work and how Proton Mail can help protect your business against them (and save your business money).
Phishing and other kinds of email-based cyberattacks
Phishing
A form of social engineering(new window), phishing(new window) describes a cybersecurity attack in which a criminal sends you an email that appears to be from a legitimate source but which is, in fact, fake. If you click on a link in the fraudulent email, you’ll download malware or be sent to a website that also looks legitimate but isn’t.
If you attempt to sign in to this fraudulent website, the criminal will get your login details.
Most phishing attacks aim to reveal your bank details, but because many people reuse the same email and password across multiple websites, subtler phishing attempts may attempt to lure victims in by masquerading as websites less likely to raise suspicion.
Spam
Over 400 million spam emails are sent per day(new window), accounting for around 84% of all email sent. Although not an “attack” per se, this avalanche of digital junk costs businesses billions in lost productivity each year. A survey(new window) found that, even then, employees spent an average of 6.5 minutes per day managing spam, amounting to a yearly productivity loss of 1.4 percent.
Lateral phishing
This devious phishing attack abuses your assumption that emails sent from within your company are not suspicious. The attacker takes over an account within your business and uses it to send more convincing phishing emails to your employees and external business contacts.
The primary aim of most lateral phishing attacks is to steal confidential company credentials. Security outfit Barracuda in collaboration with researchers from UC Berkeley and UC San Diego(new window) found that “one in seven organizations experienced lateral phishing attacks over the past seven months”.
The researchers also identified 154 compromised accounts that sent out over 10,000 phishing emails, 40% of which were to employees within the same company as the hijacked email account.
Spoofing
Spoofing attacks(new window) involve emails that use a forged sender address, making it more likely the emails will be opened. They’re usually used to deliver spam, phishing, or malware attacks.
Business email compromise (BEC)
Also known as a Man-in-the-Email scam or email account compromise (EAC), BEC attacks appear to come from a trusted source who requests a fraudulent money transfer.
Often involving a strong element of social engineering to convince the victim that the email is genuine, a typical attack purports to come from a CEO or other company executive authorized to request money transfers. However, BEC attacks can also target victims outside the business office (for example, a homeowner can be asked to make a downpayment on their property).
The FBI lists five common forms of BEC attack(new window) and reports that between October 2013 to July 2019, they have globally cost businesses $26 billion(new window) (with a 100% increase in reported losses between May 2018 and July 2019).
Spear phishing
As its name suggests, this is a variant phishing attack that targets specific individuals or small groups. The attacker usually combines careful research and social engineering to convince the victim that the email is genuine. For example, the email might discuss the victim’s role within your company.
Whale phishing (or “whaling”) is a spear phishing attack that targets a rich, famous, or powerful individual (because whale = “big phish”).
How can Proton Mail prevent phishing?
Cybercrime is a multi-billion dollar industry that encompasses a broad range of threats. Effective prevention requires employing a wide-spectrum approach to protecting your business.
This includes strong anti-malware defenses, robust security policies(new window) (with appropriate education and training for staff), and continuous monitoring of your systems. Deployed as part of a holistic approach to cyberdefense, Proton Mail can help defend against some of the most common email-based cybersecurity threats.
Multiple email addresses
An effective way to defend against email attacks is to limit the number of people who know your real email addresses. Proton allows you to create multiple email addresses (including email addresses using your company’s custom domain with a Proton for Business plan), plus an unlimited number of +aliases.
Learn about using multiple email addresses with Proton Mail
You could, for example, set up an email address to give out freely, plus one or more email addresses you only use for sensitive communications, such as an email address you only use for your bank.
In this example, any email claiming to be from your bank that does not use your dedicated banking email address is almost certainly a phishing attempt(new window).
And now that Proton has joined forces with SimpleLogin(new window), it’s even easier to hide your real addresses with on-the-fly email aliases that you can easily create, delete, block, and manage.
Link confirmation
This simple but effective phishing defense, enabled by default in all our apps, asks you to confirm that you wish to open an external link from an email. We strongly advise that you always take this opportunity to read the full link to see whether it’s genuine.
Learn more about link confirmation
Address verification
This advanced feature allows you to manually trust PGP keys for specific contacts. This can benefit your business’s cybersecurity by giving you full control over which keys you choose to trust.
Learn more about address verification
Lock icons
You can easily identify the encryption status of emails you receive using lock icons shown on each email.
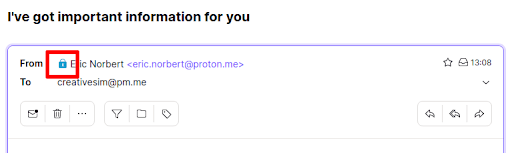
- A blue lock means the secure email was sent from a Proton Mail address. It is not possible to spoof emails(new window) from Proton Mail accounts.
- If your organization uses Proton Mail, this also provides a guarantee that someone within your organization sent the email.
- A green lock denotes a PGP-signed message. A PGP signature guarantees that the sender is genuine and that the message hasn’t been tampered with.
- A blue or green lock with a checkmark shows that you have manually chosen keys to trust with this contact (Address verification).
Learn more about how to check encryption status using lock icons
Learn more about how to protect yourself from phishing attacks(new window)
Data breaches
A data breach occurs when sensitive information held by a company is made available in an unauthorized way.
Data breaches can result in competitors gaining access to what should be privileged information about the internal workings of your company. However, the most devastating, high-profile, and common data breaches are when a company leaks personal details belonging to users and customers.
For example, in July 2022, Uber admitted to a 2016 data breach(new window) that affected 57 million passengers and drivers and that it paid the attackers $100,000 to keep the breach secret. Even more dramatically, T-Mobile suffered a data breach in 2021 that affected some 76 million users, resulting in a $350 million settlement to a class action lawsuit(new window).
How can Proton Mail prevent data breaches?
End-to-end and zero-access encryption
Emails sent between Proton users are end-to-end encrypted (E2EE). It is also possible to send E2EE emails to non-Proton users using PGP or Password-protected Emails. This means they are encrypted on your device and can only be read by the intended recipient. No one else, including us, can read them.
We have no control over how non-E2EE emails sent to people who don’t use non-Proton Mail are stored on their provider’s servers, but when stored on our servers, they are secured using zero-access encryption. That is, they are encrypted using your public key, so only you can decrypt them. Again, no one else, including us, can read them.
End-to-end encryption and zero-access encryption ensure no cybersecurity attack can target your company emails for corporate secrets or confidential customer information.
Learn how encrypted email works (new window)
Phishing protection
Data breaches can be accidental, but most result from deliberate cybersecurity attacks. Malware and brute force attacks are common methods used for such attacks, but phishing is also a big culprit(new window).
As discussed above, Proton Mail includes multiple features designed to combat phishing and keep your data safe.
Learn more about how to prevent a data breach(new window)
To learn how Proton Mail can help protect your business, contact our sales team at enterprise@proton.me.
Final thoughts
Cyberattacks are on the rise, and when implemented as part of a regimen of robust security measures, Proton Mail can be effective at protecting your valuable data from breaches and ensuring your company doesn’t fall victim to phishing attacks.