Over the past year, hackers have been using new and clever techniques to steal people’s online data. At Proton, we’ve been monitoring these evolving strategies and updating our defenses to stay ahead of the arms race.
Often, the attacks involve new forms of phishing or social engineering, trying to exploit the weakest link in any system: people. In both cases, the attackers are trying to catch you with your guard down.
- With phishing attacks, hackers send emails hoping to trick you into clicking a malicious link, downloading an attachment containing malware, or entering your login details into a fake login page.
- Social engineering attacks use other forms of manipulation, like getting you to call fake customer support and divulge sensitive information that way.
Our goal at Proton is to help you keep your guard up by making security more intuitive and automatic. Your Proton Account comes with a unique set of security features, such as our Official badge(new window) and the Proton Sentinel(new window) program, that provide a high level of defense against many of the most clever new attacks.
This article lists a few of the most alarming hacker trends we’ve seen and how Proton Mail can help you stay ahead of them.
Phishing-as-a-service
You’ve probably heard of software-as-a-service — cloud-based software like Slack, Canva, or Proton that you pay for with a subscription. Well, criminal organizations don’t want to be left out of a profitable business model. One such enterprise has launched Caffeine, a “phishing-as-a-service” platform that helps low-skilled hackers launch phishing attacks to steal login credentials.
The platform currently targets Microsoft 365 users(new window) by luring them to click on a phishing link and enter their username and password into a highly convincing fake login page. The phishing email and fake login page look like this:
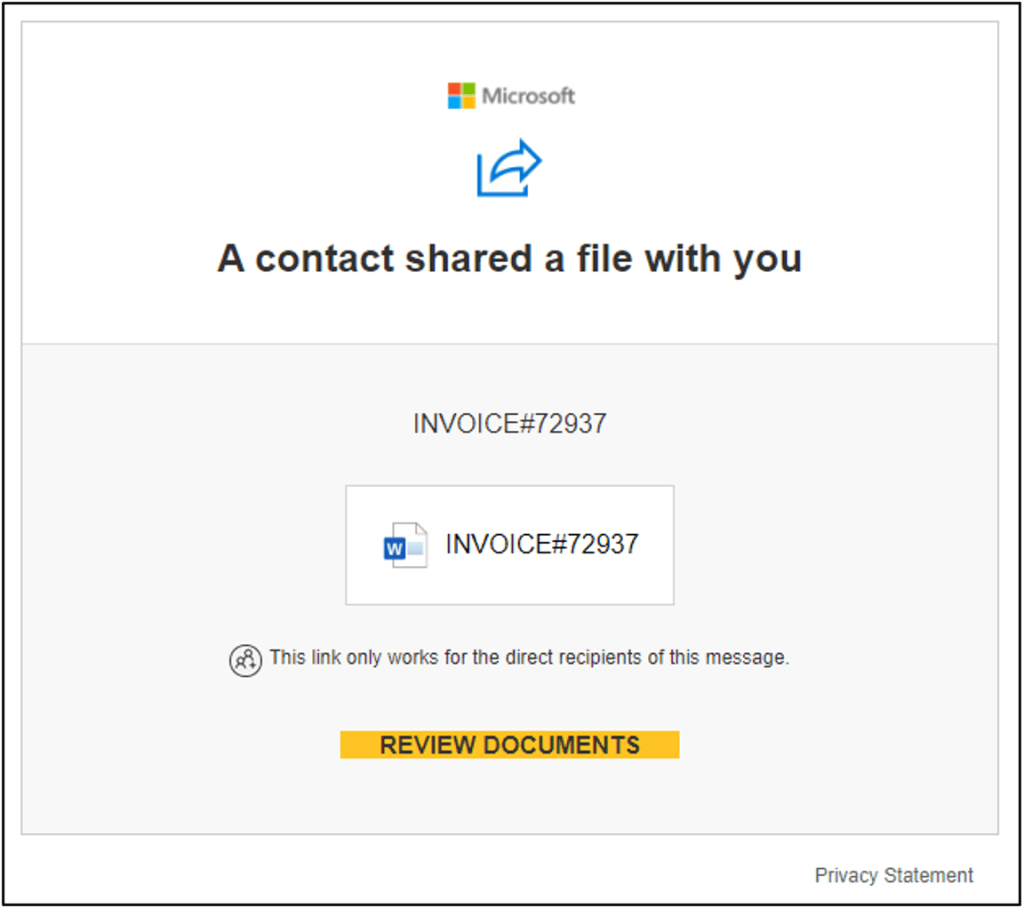
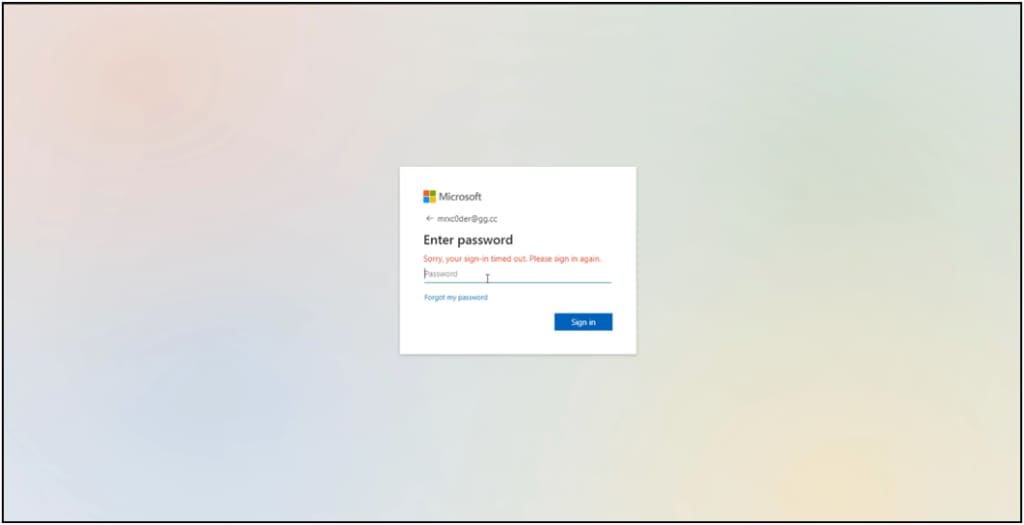
(Images via Mandiant(new window))
How Proton protects you from phishing-as-a-service
Proton Mail users are currently safe from this attack because the platform only targets Microsoft 365 accounts. However, this kind of software is likely to become more common and could eventually target Proton Accounts. If that happens, you will have multiple layers of defense:
First, the attack would likely trigger our PhishGuard filter, which flags potential phishing attacks with a red banner. Here’s a recent one sent to a Proton Mail account claiming to be an official communication from us. (There are several other red flags in this one, including the unknown email address, the unspecified recipient field, the low-quality email contents, and the lack of an Official badge.)

If the phishing attack still evades detection, there are two other lines of defense. First, you can enable link confirmation(new window), which displays the link you’re about to visit and asks you whether to proceed.
And finally, if you still somehow get tricked into entering your username and password into a fake login page, the hackers will not be able to access your data if you have two-factor authentication enabled(new window). 2FA is a must for all your accounts to prevent unauthorized access.
QR code attacks
QR codes present a unique challenge for cybersecurity because they are ubiquitous and often harmless — but they’re nearly impossible to verify as legitimate prior to scanning them. Worse, hackers are now sending emails containing only embedded images and no text. Because spam filters often depend on text scanning, these can evade detection. One of the images is a QR code that points to a fake login page or a phone number to call, leading to a social engineering scam.

(Image via Inky(new window))
How Proton protects you from QR code attacks
Proton’s custom-built PhishGuard system(new window) is designed to detect and flag potential threats without relying on scanning the contents of emails (since we can’t see your messages because of end-to-end encryption). This means image-based attacks are no more effective in Proton than any other phishing emails. PhishGuard is 70% more effective than widely used spam filters. Using machine learning, it updates automatically based on your feedback (for example, if you mark an email as spam or report phishing(new window)). On top of that we have a team of mail delivery specialists working 24/7 to analyze and adjust our systems to catch new phishing and spam campaigns that could be missed by our automatic detection.
Additionally, Proton Mail also offers a security setting that lets you turn off loading images(new window) by default. If an email is mostly or entirely composed of embedded images, this should alert you the email is likely phishing.
In general, you should never scan QR codes if you aren’t sure where they came from, and you should always check the URL of the page you land on afterward. Downloading apps from QR codes is also risky. It’s best to get apps from your app store.
Multi-factor authentication (MFA) fatigue
The increasing popularity of two-factor authentication has been tough on hackers. With 2FA enabled, stealing usernames and passwords isn’t enough. They need to get past your authenticator app or one-time passcode, too.
One emerging way hackers do this is through an attack called multi-factor authentication (MFA) fatigue. This technique targets authenticator apps with push notifications. After obtaining a victim’s login details, they try logging in multiple times in a row, triggering a barrage of requests to approve access. After a while, some people may click accept to make the notifications go away. This attack has led to high-profile breaches, such as the LastPass data breach(new window) earlier this year.
How Proton protects against MFA fatigue attacks
Proton Mail doesn’t support push notification 2FA. In fact, our password manager Proton Pass(new window) doesn’t use push notifications either, relying on auto-filling a one-time password instead. So MFA fatigue attacks are impossible in Proton.
If you ever see a 2FA request you didn’t authorize, change your password for that account.
Final thoughts
Cybersecurity is always an arms race, and this article only covers a fraction of the attacks that Proton Mail defends our community from. But being a community-supported company gives us an edge because we don’t have to worry about developing products for advertisers. Nothing distracts us from our top priority of protecting your data.
This advantage has led to groundbreaking innovations, such as Proton Sentinel(new window) and the world’s first end-to-end encrypted email forwarding feature. These are or will soon be available if you have a Proton Visionary, Lifetime, Family, Unlimited, Business, or Pass Plus plan.
But you don’t have to have a paid account to benefit from our essential security tools, such as those listed above. Sign up for a free Proton Account to start taking advantage of better security for your data.