Passwords are a necessity of the online world. They are one of the most important means of securing your digital life, preventing hackers and anyone else from accessing your bank account, email, social media accounts, and everything else you do online.
That’s why it’s vital to use strong passwords that no one else can guess. It’s also important not to reuse passwords across multiple websites and services because if an adversary obtains your login details from one site (for example, from a data breach), they’ll be able to use those details to access all your other services that share the same login details.
This is known as credential stuffing(new window), and it’s one of the most common attack vectors used by criminal hackers.
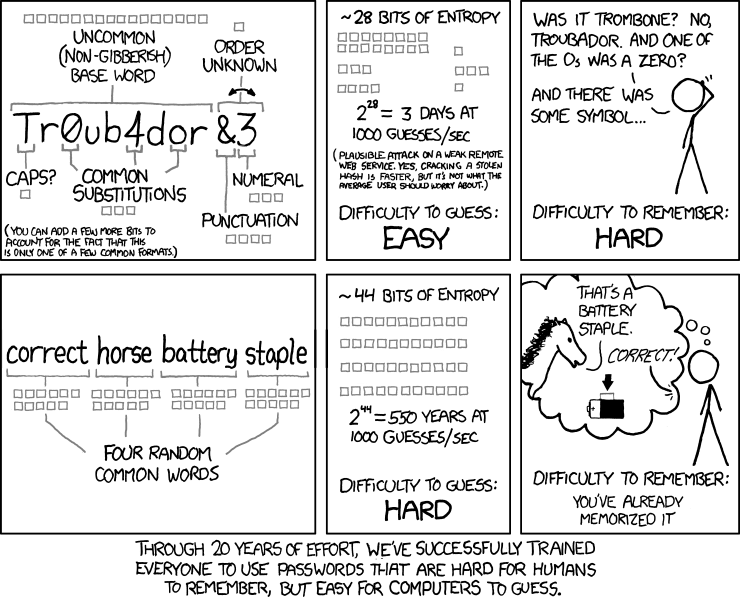
A truly secure password requires the use of mixed caps(new window), numerals, and symbols, and should be at least eight characters long (the longer, the better). Unfortunately, evolution didn’t prepare the human brain for memorizing strings such as kf6Tg&M)2D*7, let alone multiple such strings for every web service we use. As always, xkcd has a comic that explains things well:
Fortunately, computers are very good at memorizing this kind of information.
What is the purpose of a password manager?
A password manager is a computer program (app) that generates secure passwords and securely stores them for you. It will also store passwords you create yourself. Most modern password managers make it easy to enter these saved passwords (and other login details, such as your username) when you log in to websites and apps.
A password manager “remembers” your passwords (and other login details) so you don’t have to. However, because the password manager holds the keys to your entire digital life, it’s crucial that your password manager itself is secure.
Password managers themselves use a master password (which, in the case of Proton Pass, is your Proton Account password) to prevent unauthorized access. This means that if you use a password manager, you only need to remember its master password instead of remembering the passwords for all your accounts. But you should make sure that your master password is hard to guess.
How does a password manager work?
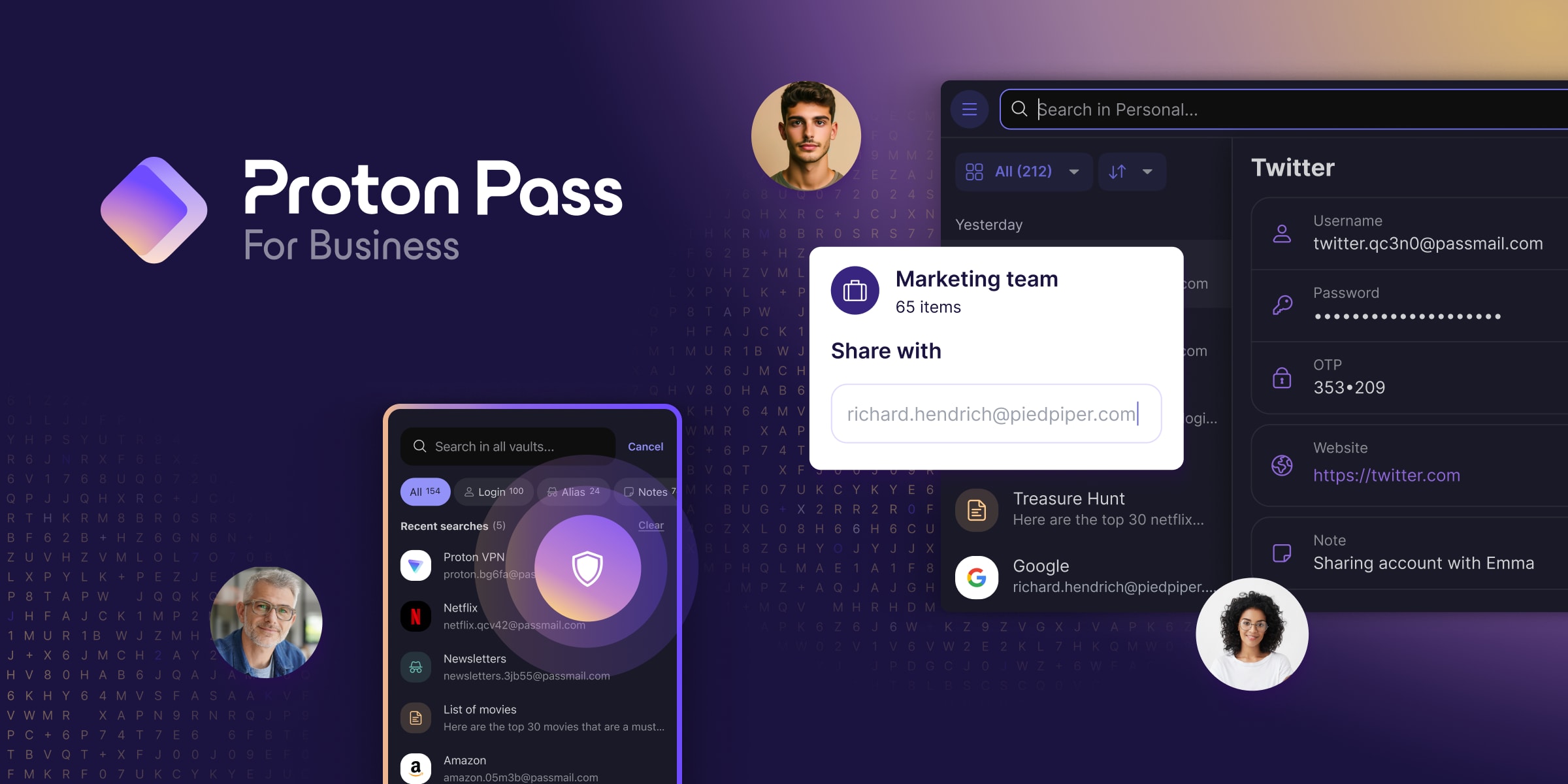
We’ll use Proton Pass as an example to show how a manager works in practice. Most password managers work similarly.
When you first sign up for a service, you’ll be asked to provide a password. You can provide your own (which the password manager will offer to store), but it’s usually easier to let the password manager create one for you. Its password will likely be much more secure than one you would think up yourself.
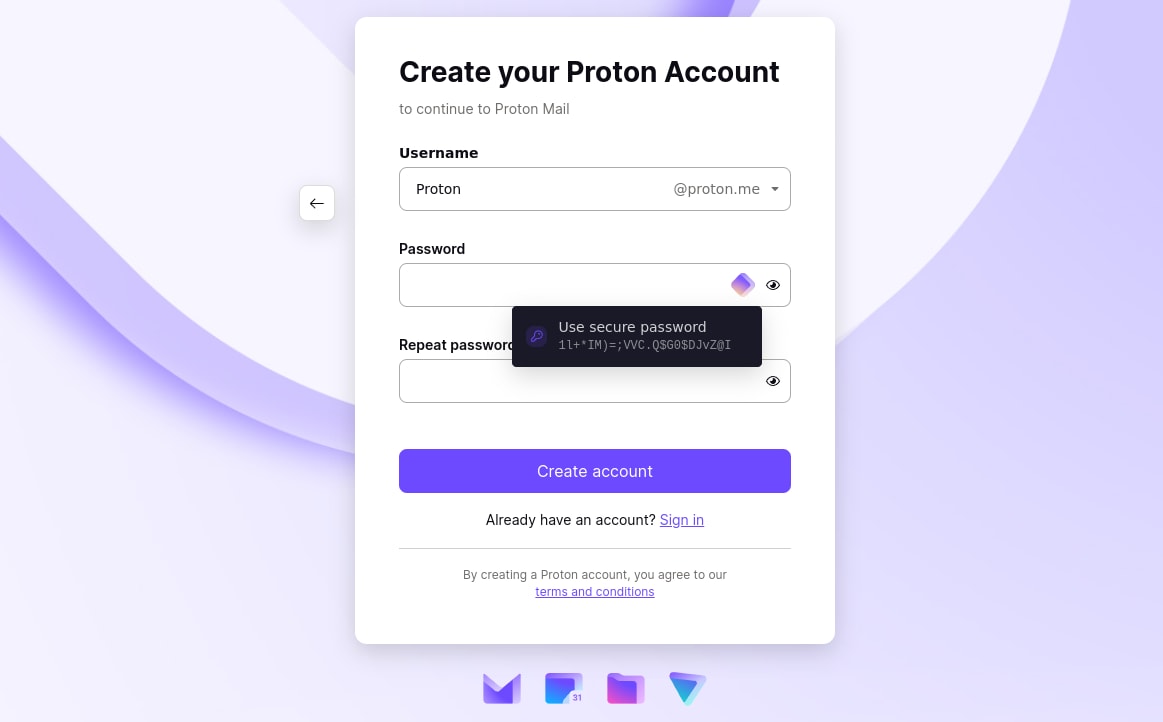
The next time you visit that website or open its mobile app, the password manager will offer to autofill your login details.
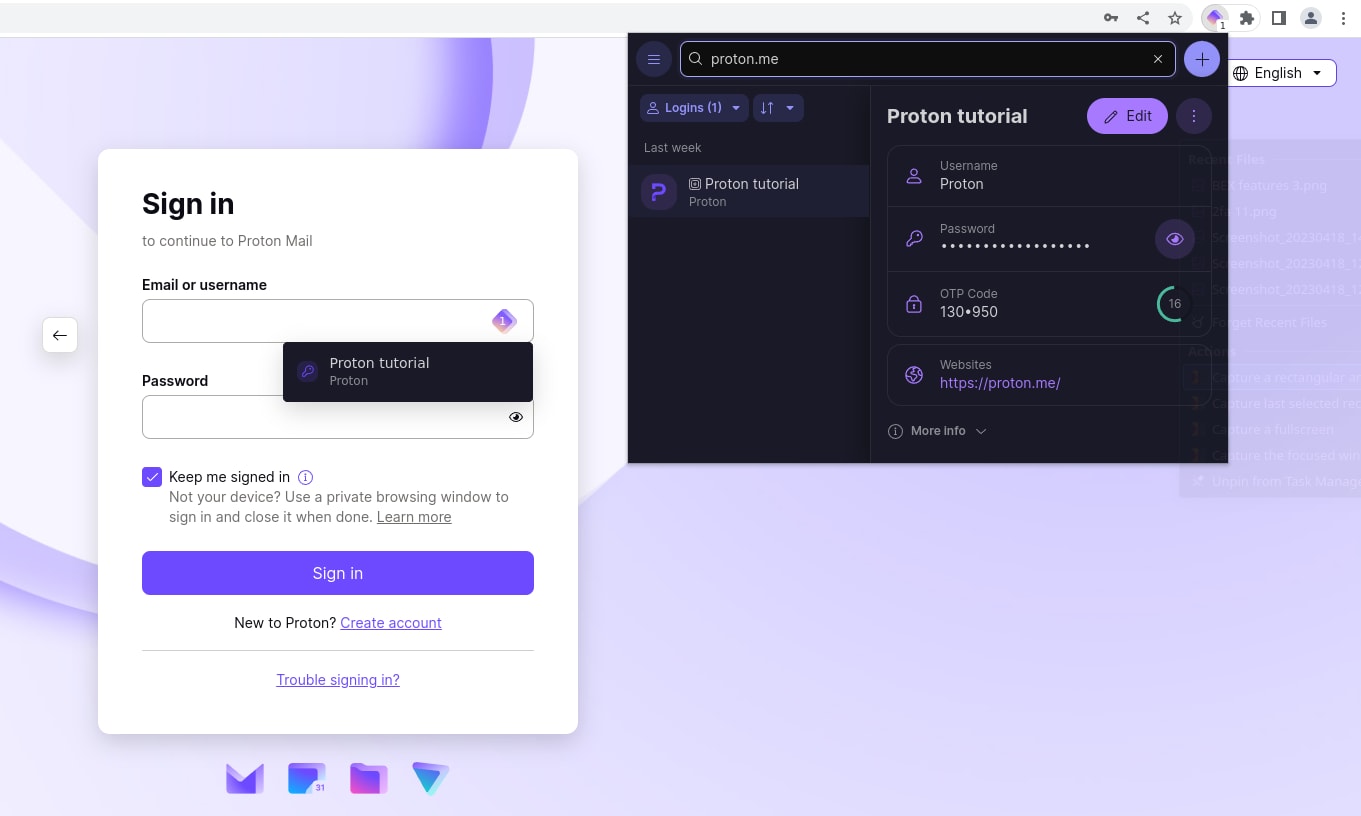
Proton Pass can even generate 2FA codes to make it easier to securely log in to your online services.
What is the main risk of using a password manager?
A good password manager will keep your passwords secure using strong encryption. However, all your passwords are secured using a single master password, so the biggest danger is that this will become compromised. If this happens, an adversary will have complete access to all your other passwords.
There are three key ways to mitigate this risk:
1. Use a strong passphrase
A sentence consisting of several random words of different lengths with spaces between each word is much more secure than any single password and much easier to remember. Diceware(new window) provides a great way to generate such a secure passphrase.
2. Use two-factor authentication
One-factor authentication requires something you know (your master password). Two-factor authentication requires an additional something that proves your identity. Unless an adversary has physical access to this thing, they won’t be able to access your accounts.
All Proton Accounts can be secured using two-factor authentication, providing a valuable second layer of defense.
Learn how to enable two-factor authentication on your Proton Account
3. Use end-to-end encryption
Many password managers store your passwords on their servers where they can access them. This makes syncing your passwords across devices easy, and if you forget your master password, it’s little trouble to recover your account (once you’ve proved your identity to them).
However, this also means the password manager can access your passwords. This isn’t a major concern if the company is reputable, but if its servers are compromised, a hacker could access the stored master password credentials and use them to decrypt your passwords.
Proton Pass instead uses end-to-end encryption. You encrypt your password vaults on your device using your Proton Account password that only you know. Proton never knows your Proton Account password, so we can’t decrypt your password vaults. And in the highly unlikely event that our servers become compromised, neither could the hacker.
Note that we have also developed several ways to recover your account if you lose your Proton Account password, without us ever having access to your password.
Learn more about account recovery methods in case you forget your Proton password
Final thoughts
Insecure and reused passwords are easily the single biggest point of failure when it comes to preventing cybercrime. A password manager makes using strong, unique passwords for all your accounts easy, meaning it’s arguably the most important tool you can use to secure your digital life.
Using any password manager is better than using none, but not all password managers are created equal(new window). Proton Pass is an end-to-end encrypted password manager brought to you by the team behind Proton Mail, the world’s most popular end-to-end encrypted email service.